The Rest of the world creates valuable data temporarily hiding it with encryption.
US Patent 8799022 replaces what makes our user's data valuable with a once used token at the point of data creation permanently protecting our user's identities and financial information.
Shutting Down that Endless Cycle of Failure
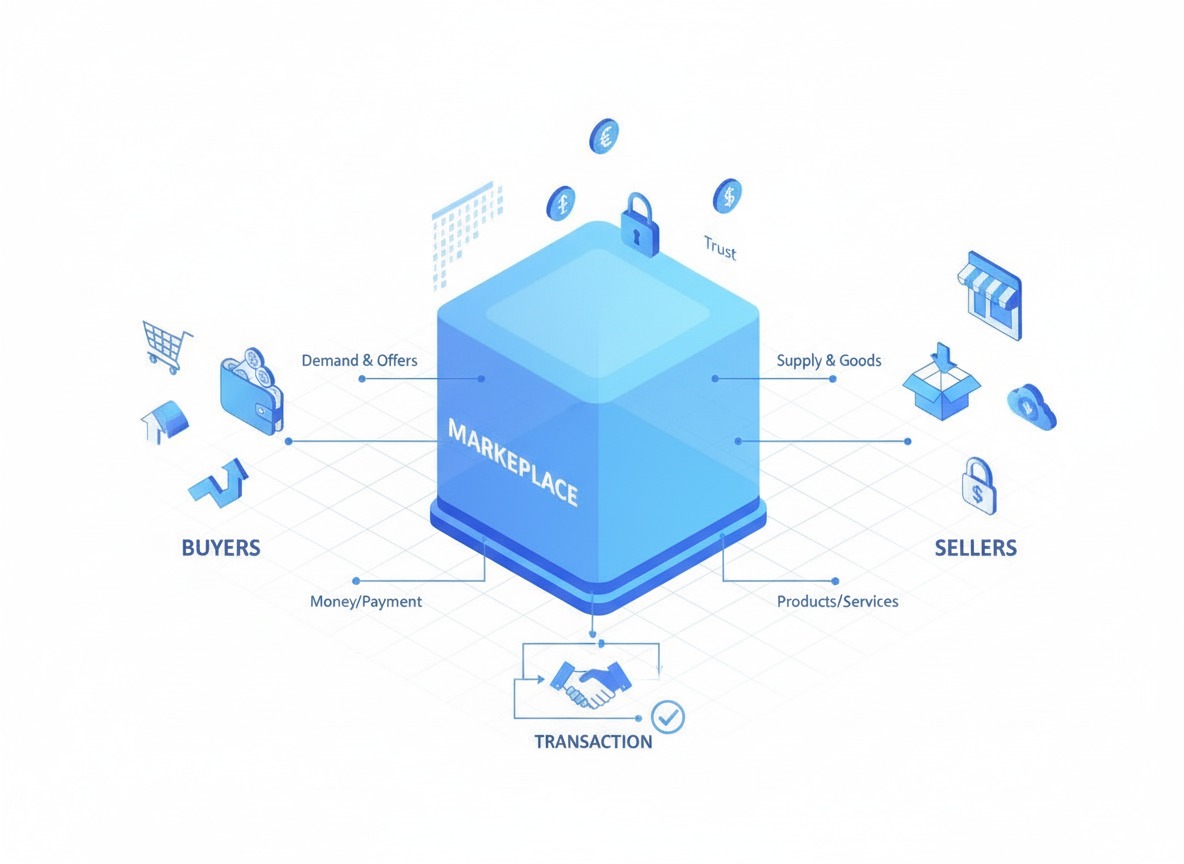
The marketplace and communication platform built with our token tech shuts down NIST's costly endless cycle of encryption failure permanently protecting our users' data as they communicate, do business and store their data.
Protecting The Past
Re processing all our user's historically encrypted data would permanently protect it as long as no one has unauthorized copies of their data to decrypt later.
Safe From the Start
Our user's data is made safe at the point of data creation because what would have made it valuable to others has been replaced by a token only valuable and useful to us allowing us to save our users money, time and effort as they use our secure SAAS marketplace and communication platform.
Actionable Intelligence For National Security
Anonymizing data as it is created at marketplace scale together with the permissions of our user agreement make nationwide actionable intelligence capabilities possible for government investigations and research without violating privacy regulations.