STRATIDGIC and the HIDDIN Marketplace and Communication Platform built with STRATIDGIC technologies are looking for an army of first adopter buyers and sellers to help us kick the tires on our pre-launch version of these technologies as we roll them out and adapt them to each communication and transaction processing channel and customize them for each industry type. STRATIDGIC and the HIDDIN Marketplace and Communication Platform built with STRATIDGIC technologies are looking for an army of first adopter buyers and sellers to help us kick the tires on our pre-launch version of these technologies as we roll them out and adapt them to each communication and transaction processing channel and customize them for each industry type.
Buyers we need your feed back on what works and especially on what does not. Sellers we need more than just your feed back we need the help of your accountant. Your accountant can help maintain the balance between your operations limited ability to scale quickly and the HIDDIN Marketplace's digital platforms ability to scale your sales too quickly.
The only thing that might be worse than not having enough sales is selling more than you can afford to bring to market. You will only get one shot at a first impression with a new customer and you want that experience to be one that promotes a long term relationship. That is the kind of relationship we want with you and why we need your help with this pre-launch to get a chance at a good impression with everyone that will come after you.
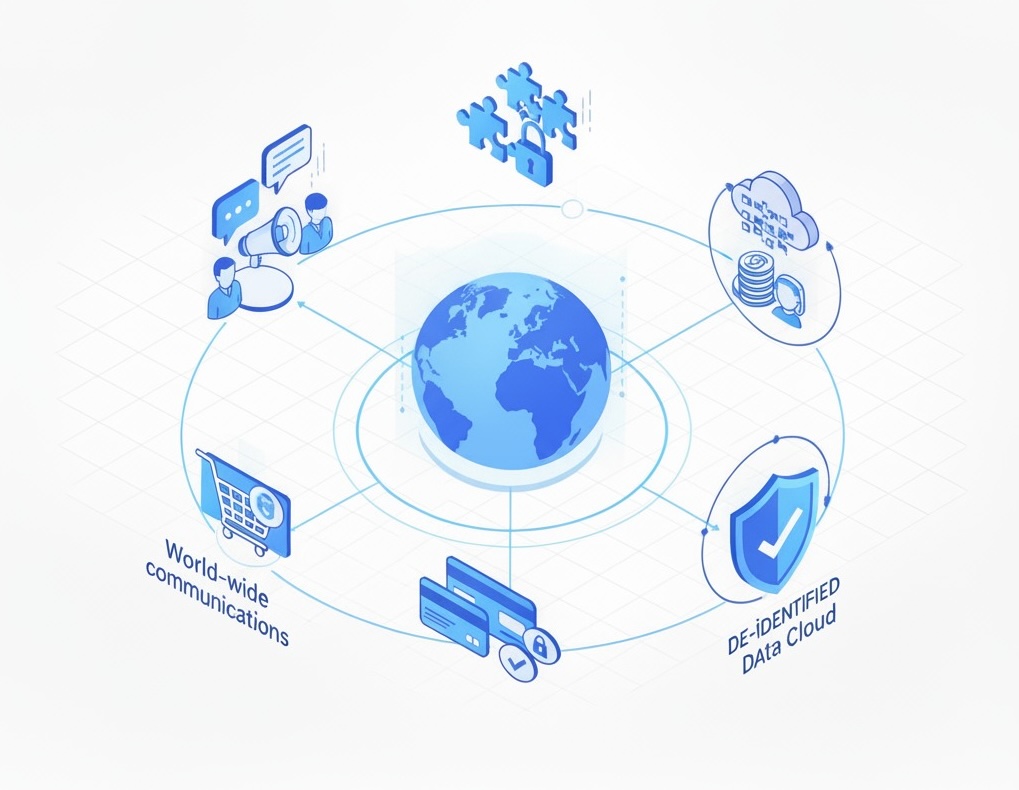
This pre-launch is not just the introduction of a few new technologies it is part of a much greater effort to help make sure that we the people will finally take control of our identity, contact and marketing information. Then control our data in the future. Right now everyone we have ever done business with has collected identity, contact, and marketing information about us and likely sold it to others. It is never complete, never up to date, neither secure nor very useful. They control it and we the people do not.













.png)